The ABCs of Vulnerability Assessment: A Beginner’s Guide

In today’s digital age, where the cyber threat landscape is constantly evolving, safeguarding your organization’s digital assets is paramount. One essential tool in your cybersecurity arsenal is vulnerability assessment. Whether you’re new to the field or looking to deepen your understanding, this beginner’s guide will take you through the ABCs of vulnerability assessment and why it’s crucial for your organization’s security.
“A” is for Assessment: What Is Vulnerability Assessment?
At its core, vulnerability assessment is a systematic process of identifying, evaluating, and prioritizing security weaknesses in your digital environment. These weaknesses, or vulnerabilities, can be found in software, hardware, configurations, or even human behavior. Vulnerability assessment helps you uncover potential entry points for cyber threats and take proactive measures to mitigate risks.
“B” is for Benefits: Why Do Vulnerability Assessment?
Key Benefits from Vulnerability are:
- Risk Mitigation: Identifying vulnerabilities allows you to address them before cybercriminals exploit them, reducing the risk of security breaches.
- Compliance: Many industries and regulations require regular vulnerability assessments to ensure data protection and compliance.
- Resource Optimization: Prioritizing vulnerabilities helps allocate resources efficiently, focusing on critical areas that need immediate attention.
- Continuous Improvement: Regular assessments promote a culture of ongoing security improvement within your organization.
“C” is for Comprehensive Process: How Does Vulnerability Assessment Work?
The comprehensive process of conducting a Vulnerability Assessment includes the following steps:
- Preparation: Define the scope, assets, and goals of your assessment. Decide whether you’ll use automated tools, manual testing, or a combination of both.
- Scanning: Automated tools scan your systems and networks to identify vulnerabilities. They analyze configurations, software versions, and patch levels.
- Analysis: After scanning, experts analyze the results to distinguish false positives from actual vulnerabilities. They assess the potential impact and exploitability of each flaw.
- Prioritization: Vulnerabilities are ranked by severity, likelihood, and potential impact. This prioritization helps you address the most critical issues first.
- Remediation: Develop a plan to patch or mitigate vulnerabilities. Implement changes to improve security and reduce risk.
- Validation: Re-assess and validate the effectiveness of your remediation efforts to ensure vulnerabilities are resolved.

“D” is for Documentation: Record Everything
Accurate documentation is essential in vulnerability assessment. Maintain detailed records of your assessments, including findings, remediation actions, and validation results. Documentation not only supports compliance but also provides a historical view of your security posture.
“E” is for Education: Knowledge Is Power
Invest in ongoing education for your cybersecurity team. Stay up-to-date with the latest vulnerabilities and attack techniques. Encourage your team to participate in training and certifications to enhance their skills.
“F” is for Frequency: Regular Assessments Are Key
Cyber threats evolve continuously, making regular vulnerability assessments critical. Conduct assessments on a schedule that suits your organization’s needs, whether it’s monthly, quarterly, or annually.
Predictive: Your Cybersecurity Ally
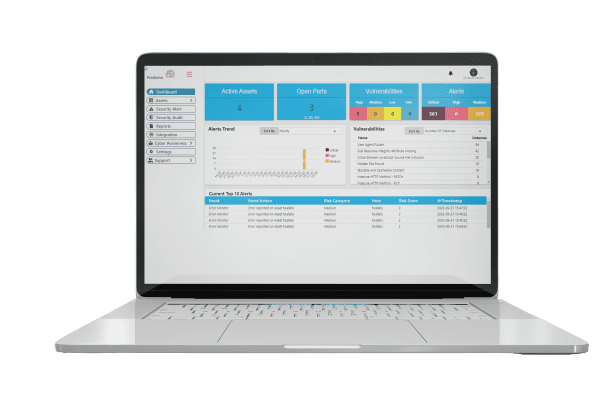
Predictive, Tisalabs’ advanced cybersecurity solution, is your ally in the quest for robust cybersecurity. By embracing Predictive, you can supercharge your vulnerability assessment efforts:
- Advanced Scanning: Predictive offers cutting-edge scanning capabilities, allowing you to identify vulnerabilities and weaknesses with precision and speed.
- Automated Reporting: Say goodbye to manual reporting. Predictive automates the generation of detailed reports, streamlining your assessment process.
- Real-Time Monitoring: Stay ahead of potential threats and vulnerabilities with Predictive’s real-time monitoring features. Receive alerts and notifications as soon as anomalies are detected.
In conclusion, vulnerability assessment is a cornerstone of effective cybersecurity. It empowers you to identify and address security weaknesses proactively, reducing the risk of breaches and data loss. As you embark on your journey to bolster your organization’s security, remember the ABCs of vulnerability assessment, and let Predictive by Tisalabs be your trusted companion. With Predictive, you can streamline and enhance your vulnerability assessment processes, making your cybersecurity efforts even more effective and efficient. Embrace Predictive, and take your cybersecurity to the next level. Stay vigilant, stay informed, and stay secure with Predictive by Tisalabs.
Related Posts


